How Security Events Should be Managed in Video Management Software
Perimeter intrusion detection sensors and video management software (VMS) make a perfect pair. Without detection capabilities, a site’s video surveillance system will only passively record intrusion events. Intrusion sensors, on the other hand, detect and locate intrusions, but without human assessment of the live, unfolding situation, the ability to mount an effective response will be limited.
When deployed together as part of a physical protection system (PPS), a VMS closely integrated with perimeter intrusion detection sensors becomes a powerful combination, providing operators with the critical information needed for obtaining situational awareness, to know what is happening where, and to optimize the use of human resources when responding to events.
In this article, we look at the key features security and video management software (SMS/VMS) need to support to achieve the full potential of integrating perimeter intrusion detection sensors with video surveillance software.
Graphical Zone and Location Data
Having intrusion alarms graphically displayed on a map provides a clear course of action for security personnel when responding to potential threats. In addition, the system should be able to track multiple intrusions, so that operators can recognize moving or multiple intruders.
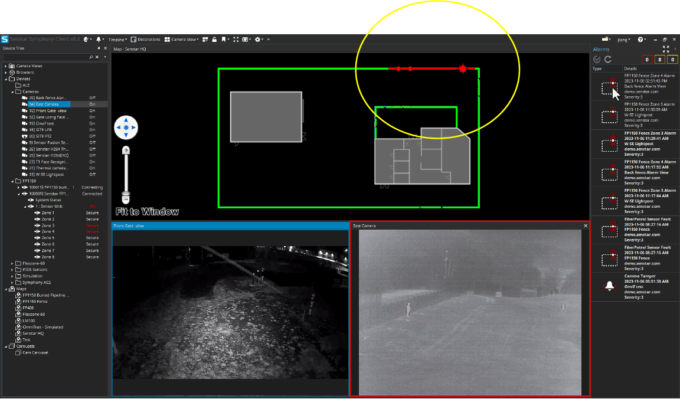
The Senstar Symphony Common Operating Platform includes built-in support for Senstar perimeter intrusion detection sensors, enabling the precise location of intrusions to be displayed on maps alongside camera panels.
Linking Alarms to Multiple Camera Videos
To reduce the time required for operators to fully assess the security situation, the system should be able to link perimeter alarms with multiple camera feeds, enabling them to immediately see the full security context of the threat.
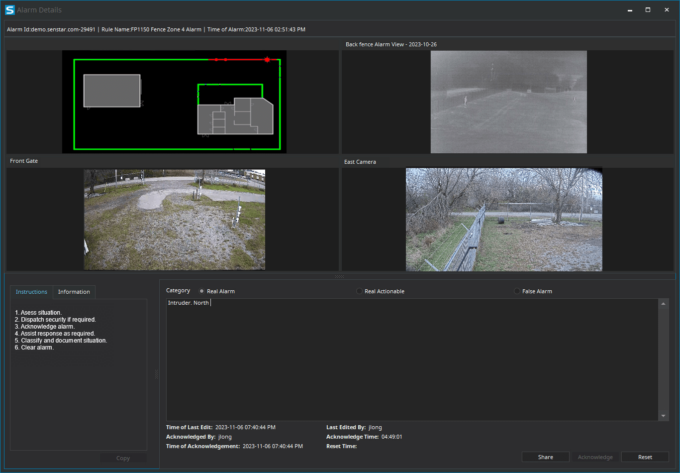
Senstar Symphony can link intrusion alarms to multiple camera feeds, ensuring security operators maintain situational awareness when responding to an alarm.
Multi-Stage Alarm Handling
In high-security environments, a two-stage alarm process (new/unacknowledged → acknowledged → cleared/closed) helps to ensure alarms are handled according to procedure and fully investigated before being cleared.
Zone Masking
For high-activity areas such as main gates, it is often necessary to temporarily mask alarms during regular business hours to facilitate authorized access. The software should enable zone masking based on schedules or temporary operator override, with all operator actions being controlled via granular permissions and logged via audit reports.
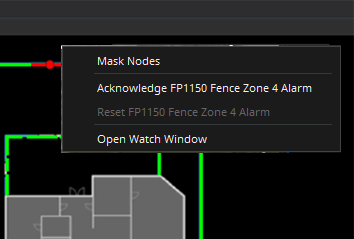
Senstar Symphony allows authorized users to temporarily mask zones for a configurable length of time.
Real-Time Sensor Status
Depending on the type of intrusion sensor, it is imperative for operators to be able to view the real-time status of each sensor. For example, a door latch should report its status as being open or closed, while a microwave sensor will remain in alarm as long as the disturbance remains in effect.
Incident Documentation
To assist post-event investigations, the software should enable operators to categorize each alarm and provide a description of the event. The descriptions must be timestamped and linked to specific video events for quick investigation, playback and/or export.
Senstar Symphony Common Operating Platform, Release 8.6
The 8.6 release of the Senstar Symphony Common Operating Platform includes new security management features designed for protecting secure environments, including critical infrastructure, correctional facilities, data centers, distribution centers, and power generation plants. For information on how Senstar Symphony can provide command and control functions at your site, contact your local Senstar representative.