Watch and Learn
Watch our videos to learn more about how Senstar can help address your organization’s security and operational challenges.
Senstar Sensor Fusion Engine
This video demonstrates how the Senstar Symphony Common Operating Platform with sensor fusion engine can improve intrusion detection capacities and defeat nuisance alarms. It includes surveillance footage of different security scenarios that show the direct, real-world benefits.
WATCH VIDEOMore Videos
View allProtect and Track
Factories, manufacturing facilities and distribution centers require around-the-clock protection. By combining video surveillance with analytics, security sensors, and data from manufacturing or logistics systems, organizations can see what is going on, detect abnormalities, and implement corrective actions.
WATCH VIDEOUnify Security and Operations
Central to our vision of consolidating security and operations is the Senstar Symphony video, security and information management platform. Senstar Symphony incorporates the latest in video analytics and artificial intelligence to provide true organization-level knowledge for better risk mitigation and business decisions.
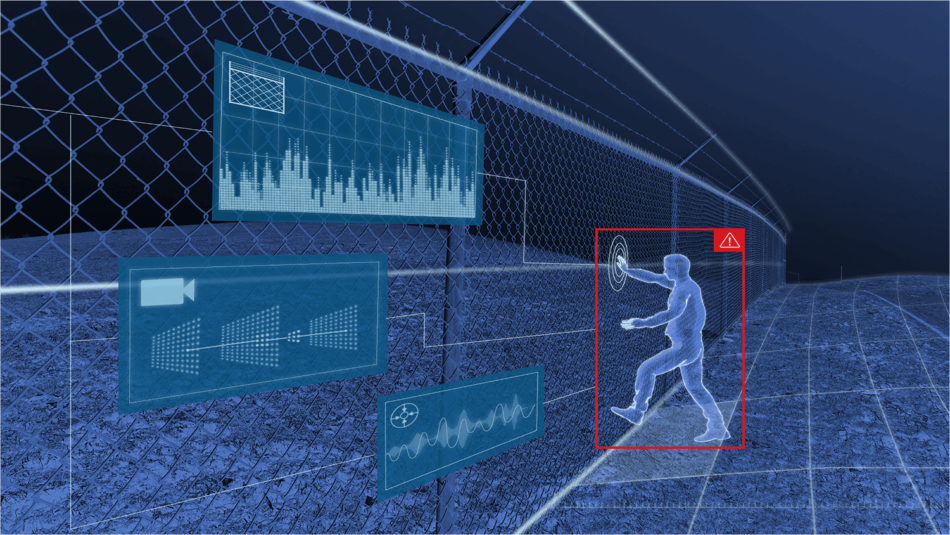
WATCH VIDEODetect and Locate Intruders
FlexZone, Senstar’s fence-mounted guided RF sensor, detects and locates any attempt to cut, climb or otherwise break through a perimeter fence. It accurately locates intrusions even when there are multiple simultaneous intrusions and in the presence of background environmental noise.
WATCH VIDEO