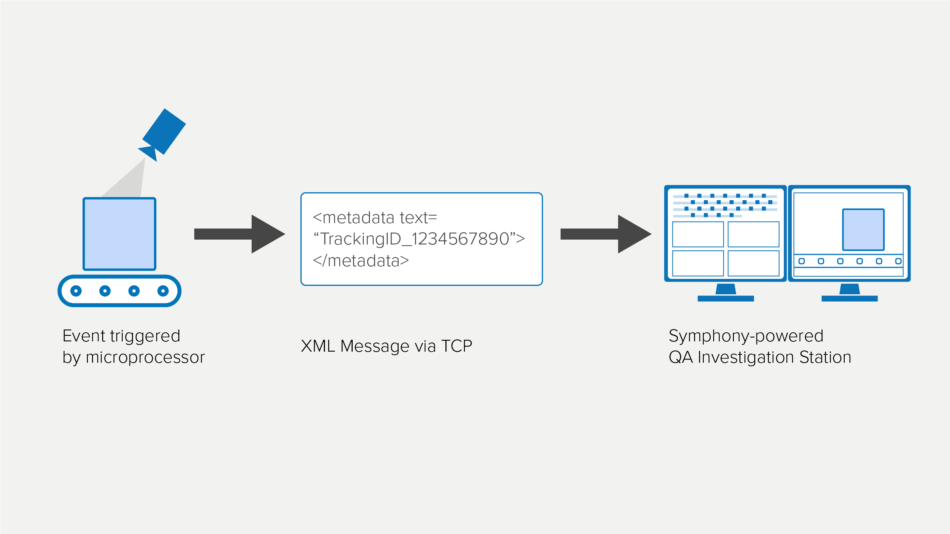
TCP Listener
The TCP Listener is a Senstar Symphony module that listens for incoming metadata over a TCP socket and associates it with an image or video, enabling organizations to use data like barcodes or serial numbers when searching for photos and recorded video. An ROI can be gained by reducing the amount of time it takes to conduct investigations and reduce warranty claims.
Visually Track Containers and Packages
Link surveillance footage to scanned data from shipping containers and packages. Resolve missing or damaged package investigations by quickly retrieving video footage of the package at key processing stages.
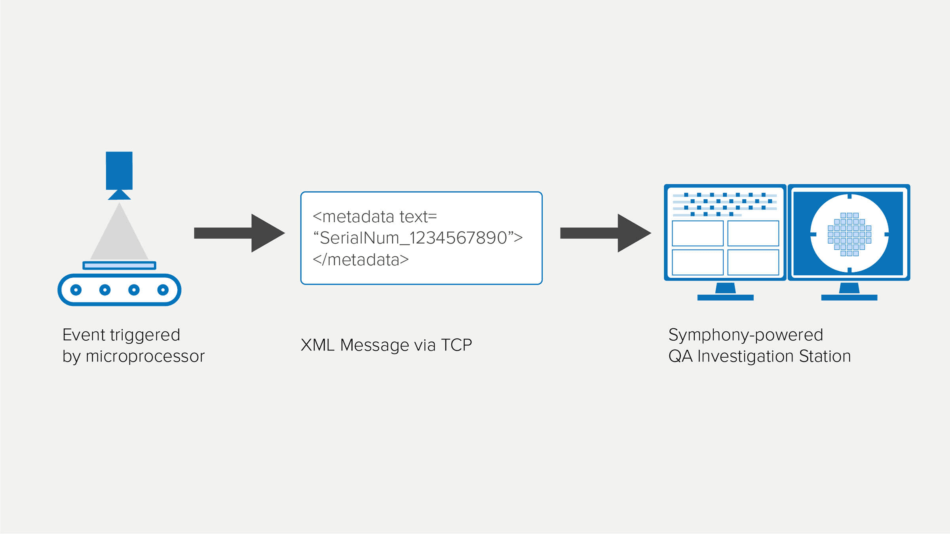
Resolve QA Issues
Use events generated by microcontroller devices on the manufacturing floor to visually document each stage of a product as it moves through the manufacturing process. Quickly find and isolate the cause of defects by viewing the product at each state along the timeline.
Additional Resources
All Video Management
Return to Category
Documentation
All Product Documents
Product Use Case
Manufacturing and Logistics
Video Management Info
View General Info
How Security Events Should be Managed in Video Management Software
Perimeter intrusion detection sensors and video management software (VMS) make a perfect pair. Without detection capabilities, a site’s video surveillance system will only passively record intrusion events. Intrusion sensors, on the...
Six Challenges in Securing Large Perimeters: Part 2
A recent article posted on securitymagazine.com summarized six challenges associated with securing the perimeters of large facilities. In our last post, we looked at the first three challenges. In Part 2...
Six Challenges in Securing Large Perimeters: Part 1
A recent article posted on securitymagazine.com summarized six challenges associated with securing the perimeters of large facilities. In Part 1 of this article, we examine the first three challenges in greater...