When Does an Event Become a Security Threat?

Every security breach boils down to one thing: unauthorized access. For this to happen, three critical elements must converge—opportunity, means, and motive. This is the crime prevention triangle, and breaking any side stops the threat cold.

Smart security professionals leverage risk analysis and Crime Prevention by Environmental Design (CPTED) to target these vulnerabilities systematically.
- Opportunity can’t be eliminated—your facility’s existence creates it. But a hardened site with minimal visible targets drastically reduces appeal to potential intruders.
- Means is countered through physical barriers like fences, locks, and bollards. Yet the harsh truth? “A fence only keeps honest people out.” Even razor wire can be defeated by determined attackers, and such extreme measures often won’t fly in civilian settings.
- Motive is where modern surveillance and detection technologies prove their worth. We can’t read minds, but behavior speaks volumes. Unauthorized entry patterns reveal intent, allowing for rapid assessment and decisive response.
The Need for Context When Inferring Motive
A potential weakness of intrusion detection technologies is a lack of full context when deciding if an event is generated by a real security threat or something that, from the perspective of the system itself, merely resembles it. We call them nuisance alarms for a reason – they distract security personnel, waste resources, and even lead to system mistrust and complacency. In the worst case, they may cause operators to ignore real threats.
For these reasons, intrusion detection solutions must be more than just an application of a given technology; rather, they need to be designed from manufacturers with the necessary real-world experience to fully understand the nature and context in which an event occurs.

Perimeter fences adjacent to public areas require new technological approaches to intrusion detection as the mere presence of individuals near the fence does not indicate an active threat.
For example, consider video analytics. By leveraging a site’s existing surveillance system, they provide a low-cost solution for automated intrusion detection. However, video lacks the full context of intrusion events – it is inherently two-dimensional and lacks “ground-zero” data, which can lead to poor performance in all-too-common situations:
- In less sophisticated analytic systems, insect movement on or near the camera can be mischaracterized as intrusion events further away, while wind shaking cameras and moving vegetation, can lead to invalid movement detections.
- Lawful nearby activity (for example, a person walking along a public sidewalk running parallel to the fence) can appear as an intrusion event, even if the person does not actually touch the fence.
- Vehicle headlights, flashlights and laser pointers can be used to overwhelm a camera’s sensor, enabling intrusions to go undetected.
- Poor visibility during extreme weather conditions like snowstorms, sandstorms, thick fog or heavy rain can wreak havoc on video quality and overall analytic performance, leading to false or (even worse) missed detections.
- Insufficient lighting can cause video analytics to be blind and not see relevant events.

Spiders, spider webs, and flying insects can degrade the effectiveness of some video analytic solutions.
Another approach to intrusion detection is fence-mounted sensors. Fence-mounted sensors are also highly cost-effective, as they leverage the fence itself for detection. One of their key strengths is that they interpret motive (intent) directly from the intruder’s actions; namely the intentional, non-natural disturbance of the fence fabric itself. Simply walking near a fence (e.g. a guard on perimeter tour) does not trigger an alarm. The fence is a logical demarcation between lawful and unlawful activity, the “red line” for determining intent. However, as with video analytics, fence sensors lack the full security context (they provide fence disturbance data at one physical location), potentially resulting in a lower detection rate in specific intrusion edge cases.
Sensor Fusion: Context-Based Decisions
Senstar’s extensive experience and comprehensive portfolio provides it with the unique ability to offer innovative solutions that are not tied to or limited by any one technology. Senstar’s Sensor Fusion Engine and the Senstar MultiSensor Cascade Plus, are unique, groundbreaking technologies that can defeat nuisance alarms once and for all while maintaining the highest Probability of Detection (PD).
In both products, an AI-powered sensor fusion engine uses context to intelligently infer motive and detect intruders. More than just a simple Boolean logic integration, the sensor fusion engine accesses low level data from a range of sensors to correctly characterize perimeter threats:
| Event | Sensor Fusion Engine Characterization |
| Regular fence climb | Security threat (intrusion detected) |
| Person or object moving towards perimeter | Potential threat (pre-alarm condition) |
| Person climbing, cutting, or lifting fence | Security threat (intrusion detected) |
| Person or object entering a restricted area | Security threat (intrusion detected) |
| Insect on camera lens appearing to “climb” fence | No threat (no alarm) |
| Severe storms (winds, hail, rain, etc) | No threat (no alarm) |
| Loose fence signage or damaged fence fabric | No threat (no alarm) |
| Snowdrifts against the fence | No threat (no alarm) |

Senstar MultiSensor Cascade Plus uses context to intelligently infer motive and detect intruders.
Senstar Sensor Fusion Engine
Senstar’s Sensor Fusion Engine combines the best of fence sensors and video analytics and enhances them with AI-powered sensor fusion. It is licensed per-camera, meaning you can use it to protect an entire perimeter or to enhance specific perimeter segments that are either high-risk or prone to nuisance alarms. It can be deployed as a drop-in solution or as part of the full-featured Senstar Symphony Common Operating Platform:
- Drop-in solution – Pre-installed on a physical security appliance (PSA), the Sensor Fusion Engine generates zone alarms when valid intrusions are detected. The PSA communicates with third-party Video or Security Management Systems (VMS/SMS) via SDK integrations, TCP/IP messages, or hardware I/O.
- Senstar Symphony video analytics – By adding fence sensors to the system, the precise intrusion location is displayed on a graphical map and the alarms can be used for camera call-up and to trigger customizable action sets via Senstar Symphony’s rules engine.
Senstar MultiSensor Cascade Plus
Senstar’s MultiSensor technology represents a significant advancement in perimeter protection. A compact, intelligent device, It uses an AI-powered embedded Sensor Fusion Engine to perform a threat analysis based on the best data available from a range of sensors:
- Short-range radar for tracking object movement and size
- Integrated video analytics for visual verification
- Dual PIR sensors for enhanced detection
- Advanced vibration sensing through precision accelerometers
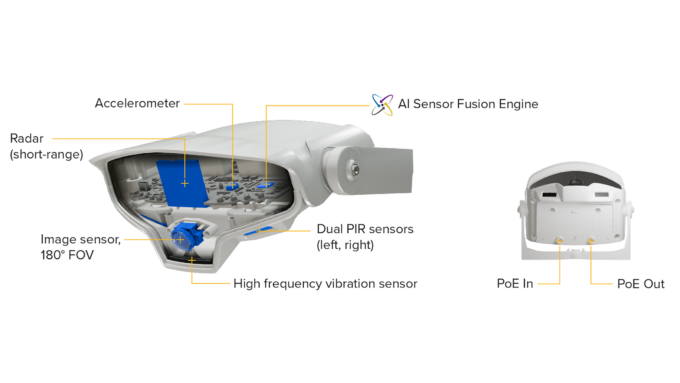
This multi-modal approach ensures that security threats are detected with exceptional accuracy while virtually eliminating nuisance alarms. The system’s ability to synthesize data from different sensor types creates a robust detection mechanism that maintains effectiveness against sophisticated attacks as well as with challenging environmental conditions.
Its compact size and PoE extension/daisy chain capabilities enable it to be used as a drop-in solution for enhancing existing security capabilities in problematic areas as well as providing a comprehensive “wall of detection” for larger perimeters.
A Better Approach to Perimeter Security
To improve performance and avoid the limitations of individual technologies in specific edge cases, new approaches to intrusion detection are required. By understanding context, Senstar’s next-generation sensor fusion and MultiSensor products can differentiate between a benign event and real security threat. Senstar technology adds intelligence to a site’s security system, empowering security personnel by providing them with relevant and timely information about perimeter activity.
| Security Application | Product Recommendation |
| Perimeter fencing with existing FlexZone deployment | Add Sensor Fusion upgrade to problematic or high-security zones to improve detection and eliminate nuisance alarms |
| Perimeter fencing monitored with only cameras and video analytics | Add FlexZone with Sensor Fusion upgrade to augment intrusion detection capabilities and eliminate nuisance alarms |
| Unprotected, high-risk, or problematic section of the fenced perimeter | Add a daisy chain of Senstar MultiSensor devices along fence line to detect intrusions and/or nearby activity |
| Open areas or gates | Add Senstar MultiSensor to create a solid “wall of detection” across open area. |
| Doors, entrances, large windows | Add Senstar MultiSensor above area to protect |
| High-value assets | Monitor area for activity and intrusions with Senstar MultiSensor |
For More Information
For more information about how Senstar can improve security at your site, contact your local Senstar representative.

