Data Center Physical Security: Maintaining Customer Confidence

The financial success of cloud services is predicated on customer confidence in the cloud provider’s ability to keep their data safe and available when needed. Data security is a complex subject, with many cross-functional aspects, including cybersecurity, data availability, system resiliency, data privacy, and strict physical access controls.
To demonstrate their ability to deliver on the promise of keeping data safe and available, cloud service providers commit to meeting a broad set of international, regional, and industry-specific compliance standards (ISO 27001 and SOC 2, to name a few). Transparency is a key requirement, as the results of rigorous third-party audits can be requested by customers to ensure accountability and credibility.
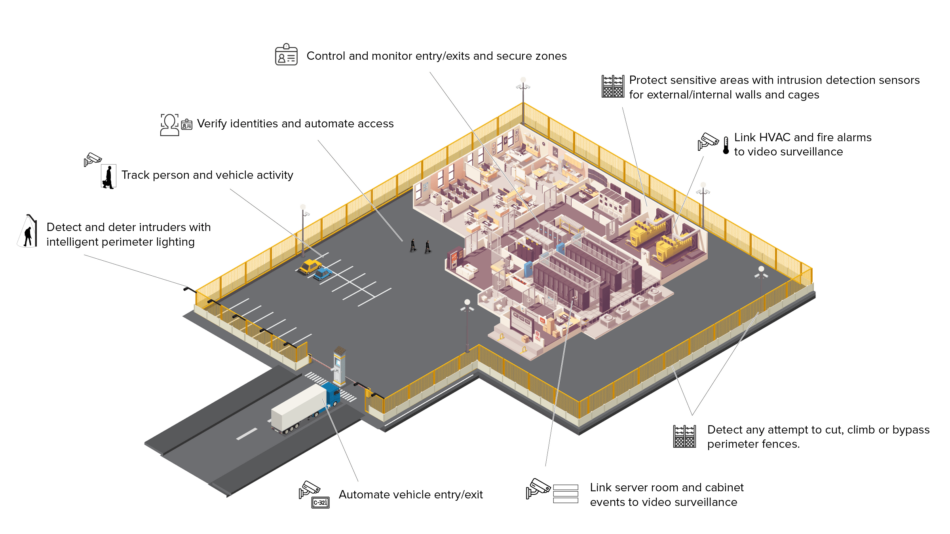
A key component of these compliance audits is the physical security of the data center itself and the implementation of strict physical access controls to customer data. For data centers, physical security can be looked at from a multi-layered “onion” perspective, one that corresponds loosely to the physical layout of the facility itself.

Senstar, with its comprehensive portfolio of video and security management software, perimeter intrusion detection sensors, electronic access control, video analytics, and metadata collection, can assist cloud service providers in keeping facilities secure while meeting compliance requirements for physically securing customer data.
Perimeter Security
Protecting the perimeter of a facility is the first line of defense and a critical part of any security plan. Senstar perimeter intrusion detection systems (PIDS) provide early warning of unauthorized entry and offer organizations the following benefits:
- Reliable and effective detection
- Low nuisance alarm rates
- Integration with deterrence devices (lights, sirens) and assessment devices (cameras, analytics, other sensors)
- Effective response to security events using critical information obtained from sensors and surveillance systems
As each site has its own perimeter security requirements, Senstar offers a range of fence, buried, and above ground sensors, ensuring optimal coverage for sites of all sizes.
Facility Management
Facility management encompasses many aspects related to the security, safety, and efficiency of the facility:
- Electronic access control: Limiting access to only approved employees and visitors is critical. Access should be granted based on the principle of least privilege – only those with valid business justifications should be allowed into the facilities. Employees should have predefined access levels based on their role, while visitor requests should be reviewed and approved by authorized personnel, with access being automatically revoked after the authorized time expires. In addition, access should be limited to only those areas specified in the approved request.
- Tracking vehicle metadata (via license plates or truck/cargo identification numbers) can help streamline operations by improving workflows and provide insight into business processes.
Server Room and Cabinet Monitoring
The monitoring of access to both server rooms and individual server cabinets is critical for data security and procedural compliance. Access to individual server rooms must be strictly controlled and monitored. In addition to controlling access via two-factor authentication, metadata from door and cabinet events can be linked to video surveillance, providing easily searchable visual records of all server maintenance as well as enhanced technician accountability.
Dataline Security
Reliable, uninterrupted communication links are vital to the core business of data centers and cloud services. Quality of Service (QoS) guarantees are a key requirement for high-end applications including video on demand and communications. Any interruptions caused by physical interference can have detrimental consequences.
Senstar’s FiberPatrol fiber optic sensor detects third-party interference (TPI) to fiber optic data links and other cable infrastructures. FiberPatrol requires just one optical fiber to detect potential TPI events anywhere along the cable’s pathway, and determines and reports the precise location of each event. Classification abilities can indicate the nature of the intrusion, including the presence of heavy machinery, vehicle traffic, machine and human digging, and direct tampering of the cable conduit. The sensor can also be used to verify the location of buried communications infrastructure and ensure redundant paths do not overlap or exist in close proximity to each other.
A Common Operating Platform for Reduced Complexity
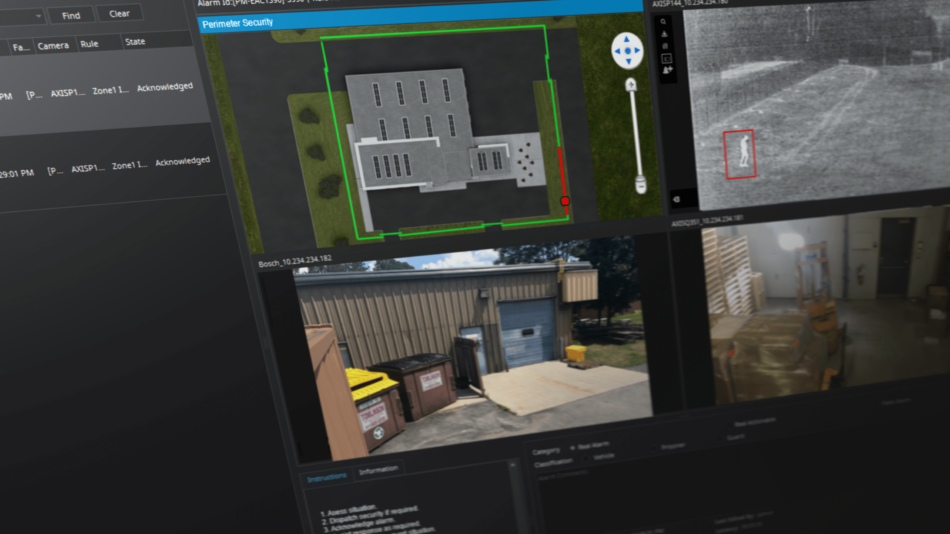
With added security and compliance monitoring comes the risk of increased complexity – integration issues, increased training requirements, maintenance difficulties, to name a few. To manage this increase in information so that organizations can make better sense of it, Senstar offers the Senstar Symphony Common Operating Platform, a modular solution for security management and data intelligence. In addition to being an open, highly scalable video management system with built-in video analytics, it includes full-featured access control and perimeter intrusion detection modules. By taking a unified, “single pane of glass” approach to command and control and deploying devices that use industry standard interfaces, cloud service providers can maintain situational awareness across distributed sites and effectively direct operations during security incidents.
For More Information
For more information on how Senstar can help secure data centers and meet security compliance requirements, download our brochure, Physical Security Solutions for Data Centers.