Mind the Gap: The Perils of Security Silos in Data Centers

In the fast-evolving landscape of physical security, data center operators face a persistent challenge: siloed security systems. A recent SIA Data Center Security Report highlights a troubling reality—”design accountability is fragmented,” with perimeter elements often managed separately from access control, video, and alarms.
Without a unified integration strategy, systems arrive in silos, creating the very vulnerabilities attackers are eager to exploit. Fragmentation is a liability, but a unified approach restores the advantage to the operator.
1. Eliminating Operational Blind Spots
When cameras, intrusion sensors, and lighting operate independently, no single system sees the complete picture. The SIA report notes that fragmented approaches lead to “operational blind spots” where critical incidents slip through the cracks.
- The Problem: An intrusion sensor triggers, but without automated “slew-to-cue” or call-up camera functionality, the operator is blind. Is it a legitimate breach or a false alarm? That split-second hesitation is the difference between prevention and an unclear threat event.
- The Senstar Fix: Senstar Symphony acts as a Common Operating Platform, automatically coordinating responses. When a sensor is tripped, Symphony receives detailed location data and triggers policy-driven actions—bringing up the right camera, adjusting lighting, and invoking security workflows (e.g. auto-locking doors)—all before the operator even has to click a mouse.
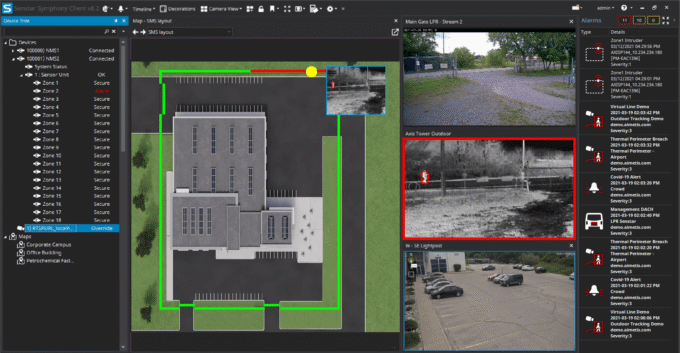
Senstar Symphony Common Operating Platform integrates perimeter intrusion detection sensors, cameras, workflows into a single “pane of glass”. The result: situational awareness without blindspots.
2. Solving the “Speed Trap”
In fragmented security environments, response follows a slow, manual pattern: receive alert → switch interfaces → find camera → verify alarm → act. Attackers use these lost seconds to advance deeper into the facility.
- The Problem: Manual correlation across multiple interfaces increases “Mean Time to React,” leaving the facility vulnerable during the most critical moments of an intrusion.
- The Senstar Fix: By integrating perimeter sensors like FiberPatrol and FlexZone natively into Senstar Symphony, the “Speed Trap” is eliminated. What was once a manual five-step process becomes a single, automated sequence.
3. Defeating Alarm Fatigue
Perhaps nothing undermines security more than alarm fatigue. Fragmented systems generate uncoordinated alerts—wind, animals, and lighting changes—without context or filtering.
- The Problem: When operators are overwhelmed by nuisance alarms, they begin dismissing legitimate threats. Once trust in a system is lost, it is difficult to regain.
- The Senstar Fix: With over 45 years of experience deploying intrusion sensors at customer sites, Senstar has a profound understanding of security environments and the negative effects of alarm fatigue. Senstar technology like environmental disaggregation, Sensor Fusion, Senstar MultiSensor, and precision LiDAR volumetric-based detection can defeat nuisance alarms once and for all. The end result: when an alarm triggers, it’s a serious situation that requires immediate investigation.
4. Ending the Maintenance Nightmare
Siloed systems create a technical debt trap: multiple support contracts, custom integrations that break during software updates, and inconsistent patching schedules.
- The Problem: What appears cost-effective during procurement becomes a financial drain over the system’s lifecycle due to high integration and maintenance costs.
- The Senstar Fix: Senstar technology incorporates an open, future-proof architecture that utilizes robust, redundant network infrastructure. Because Senstar Symphony offers native, out-of-the-box integration for all Senstar hardware and AI analytics, there are no “broken” custom links during updates. You move from managing a dozen vendor relationships to one cohesive ecosystem.
5. From “Forensics in the Dark” to Clear Evidence
After an incident, fragmented systems make investigations a complex challenge. Reconstructing a timeline across three different platforms is slow and prone to human error.
- The Problem: Inconsistent timestamps and disparate data logs weaken evidence and expose organizations to legal and compliance liability.
- The Senstar Fix: Senstar Symphony centralizes all events into a single, time-synchronized interface. Investigators see the complete sequence—from the initial perimeter breach to the final access control log—in one unified timeline. This streamlines reporting and ensures a rock-solid chain of custody for any security event.
The Path Forward
Non-negotiable security requirements and customer expectations for data centers means operators can no longer afford a fragmented security posture. With Senstar’s industry knowledge and integrated approach, that noise becomes a symphony of coordinated protection. In today’s threat landscape, that isn’t just a luxury—it’s what critical infrastructure demands.
Download our Physical Security for Data Centers Guide to learn how Senstar technology can eliminate security silos, providing comprehensive, unified solutions.

