Why Boolean Logic Is Not Sensor Fusion

Sensor fusion helps make the most of your perimeter security by maximizing the potential of all the sensors in an installation and defeating nuisance alarms. We’ve talked about what it is and the benefits it provides. However, because the described benefits of Boolean logic and sensor fusion are somewhat similar – with marketing speak often obscuring the differences – it’s easy to confuse these two technologies as being the same.
To understand why these two systems are very different, let’s look at some use cases that illuminate their differences. We’ll use one example setup with some real-life situations to see how they differ.
Sample installation
For our example, we’ll use a single building with a perimeter divided into six zones:
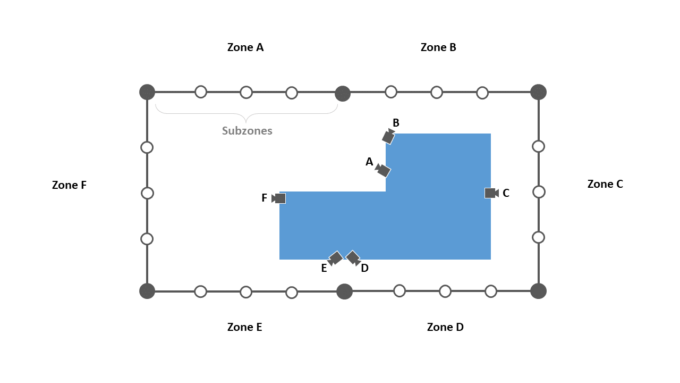
The example system is equipped with sensors that split the fence into six zones, A-F. Additionally, each zone is divided into subzones, so that every zone can report up to four distinct locations to narrow down the position of a detected disturbance.
Each zone is also monitored by a camera with analytics. That is, in addition to the camera video feeds, the cameras provide a signal when they detect people within the image.
Boolean Logic Setup
The system integration using Boolean logic requires both sensor types (fence and camera) working together to reduce nuisance alarms. This is accomplished by an “AND” operation that combines the output of the “intrusion detected” fence sensor for each zone with the “person detected” output for the camera monitoring that zone. That way, both the fence needs to move AND a person needs to be visible before an alarm will be reported. Wind or vegetation disturbances that move the fence without a visible person won’t trigger a false alarm, likewise neither will a person walking by the fence without touching it.
Sensor Fusion Setup
The sensor fusion system is similar in that it examines both sensor types to decide if there’s an intrusion attempt. However, it’s different in that it looks at the low-level data of each sensor and runs it through a pattern-matching algorithm that correlates the sensor outputs against each other. This data has been trained with machine learning algorithms so that it’s not looking for just a moving fence cable or a person-like shape, but rather a sum of sensor signal patterns that indicate problematic intent. Thus, it’s far less likely to be fooled by innocent actions that independently might appear as intrusion attempts.
Here are some examples to make this difference clearer.
Example #1 – Intruder During Wind
Example #2 – Pedestrian During Wind
Example #3 – Intruder with Ladder
Example #4 – Thunderstorm with Guard and Intruder
Example #5 – Intruder in a Snowstorm
Conclusion
Although these examples have all been designed to show the more sophisticated capabilities of a sensor fusion system, they’re not unusual situations to encounter. The flexibility and accuracy of these sensor fusion systems gives them a huge advantage when it comes to defeating nuisance alarms without needing to sacrifice site security. In fact, site security increases with better discrimination of sensor inputs, smarter correlation between sensor data, and maximum sensor sensitivity.
Given the large number of potential use cases that a thorough site security plan must manage, a sensor fusion system’s trustworthiness makes it a highly valuable part of any perimeter security system.
Read Blog #1
Read Blog #2
Senstar’s new Senstar Symphony™ Sensor Fusion Engine is driven by the Senstar Symphony™ Common Operating Platform.